What is device fingerprinting?
One efficient method for stopping fraud and protecting online transactions is device fingerprinting. To properly recognize a device, it is necessary to gather information about its hardware and software setup. The operating system, the browser variant, downloaded fonts and extensions, screen quality, timezone, and additional features that help set the device apart from others can all be included in this data. Do check device fingerprint check
The process of device fingerprinting involves gathering this data using a variety of tools, including fingerprinting browser scripts, online cookies, and other tracking methods. To find out if the device is new or has been seen previously, this data is then looked at and compared to a library of known device fingerprints.
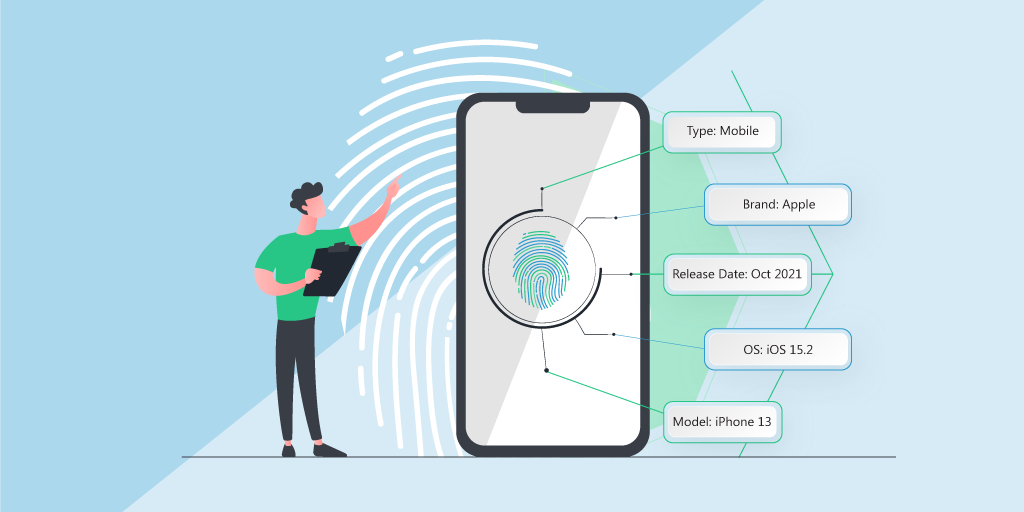
Mobile device fingerprinting
To generate a unique identity for every device, smartphone fingerprinting is a portion of device fingerprinting that concentrates exclusively on gathering data about handheld devices such as phones and tablets. While this method is comparable to fingerprinting websites and device fingerprinting, it focuses exclusively on mobile devices and the distinctive features of their software and hardware.
Data points like the OS, battery capacity, GPS status, and software and hardware specifics can be gathered via mobile device fingerprinting. These bits of information come together to form a unique identification number for every smartphone or tablet, which can be utilized for tracking it around various websites and applications.
Browser fingerprinting
A particular type of fingerprinting device known as browser fingerprinting focuses on gathering data about an internet browser and its configurations to generate a unique device identification for each user. Even if the user deletes the cookies or uses a different IP address, this data establishes a distinct fingerprint for the gadget that can be utilized to locate it online. As browser fingerprinting is a part of the larger practice of gathering gadget-specific data to locate and track devices throughout the internet, it is associated with device fingerprinting.
Why is fingerprinting used?
- To prevent fraud: Device fingerprints may be utilized to identify unusual activity patterns, such as repeated attempts to create accounts on the same device. Businesses can identify possible fraudsters and take steps to stop additional fraudulent conduct by examining device fingerprints from various accounts and transactions.
- Logging in: Device fingerprints may be added to the standard password and username combination for login authentication as an extra factor. A security alert may sound and the user may be prompted to take precautions to secure their account, like changing their password or enabling two-factor authentication to stop account takeover. This can happen if an attempt to log in occurs from a device that isn’t linked to their account.
- To view transactions: Fingerprints on a device can be used to track user transactions, including purchases and money transfers. A security warning may be generated and the user might be asked to confirm the payment or take additional security precautions if the purchase happens from a device that isn’t linked to their account.